TECHNICAL ADVISORIES
Electronic voting systems introduce significant risks to the security of our elections. The Election Crime Bureau has prepared a series of technical advisories to provide election officials with important information regarding these risks that has not otherwise been widely disseminated by government officials or electronic voting system vendors.
Technical Advisory
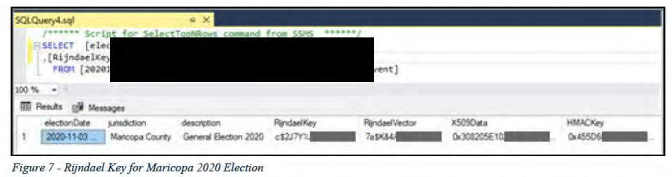
Decryption Keys
Storing decryption keys in plain text creates a major security vulnerability. If an attacker gains access to the database, they could easily obtain the keys and use them to decrypt sensitive election data such as voter registration information, ballot designs and configurations, and vote tallies and results.
Read ECB AdvisoryTechnical Advisory
Center for Internet Security
The Center for Internet Security (CIS) manages the Election Integrity Information Sharing and Analysis Center (EI-ISAC) under contract to the Department of Homeland Security (DHS) to secure election systems which we are told are not connected to the internet. In this capacity, CIS has privileged access to sensitive election records with negligible public oversight due to its status as a Non-Government Organization (NGO). Significant public trust has been placed in this organization. We believe that the general public should be informed as to the risks associated with this trust.
Read ECB AdvisoryTechnical Advisory
Internet Connections
Internet connections to/from components within an election system compromise the security of elections. Physical transfers of election records such as post-election results are secured with the application of configuration-controlled seals and bipartisan signatories. In contrast, digital transfers of election records such as post-election results occur regularly without any bipartisan oversight and are often performed/shared with Non-Government Organizations (NGO) not subject to any substantive public oversight at all. In order for the general public to trust the integrity of election outcomes, it is imperative that digital record transfers using internet connections feature security protocols commensurate with the precautions used for physical data transfers.
Read ECB AdvisoryTechnical Advisory
CISA Amber Alert
This report by the Cyber Security and Infrastructure Security Agency (CISA) provides analysis, findings, and recommendations derived from non-attributable cybersecurity trends observed between November 3, 2019, and November 3, 2020—Election Year 2020 (EY20)—among Election Infrastructure (EI) Subsector entities subscribed to services provided by CISA.
CISA’s analysis of the available data for assessed EI entities found:
• 76% of EI entities for which CISA performed a Risk and Vulnerability Assessment (RVA) had spearphishing weaknesses, which provide an entry point for adversaries to launch attacks;
• 48% of entities had a critical or high severity vulnerability on at least one internet-accessible host,4 providing potential attack vectors to adversaries;
• 39% of entities ran at least one risky service on an internet-accessible host, providing the opportunity for threat actors to attack otherwise legitimate services; and
• 34% of entities ran unsupported operating systems (OSs) on at least one internet-accessible host, which exposes entities to compromise.
Technical Advisory
Perjury Allegations
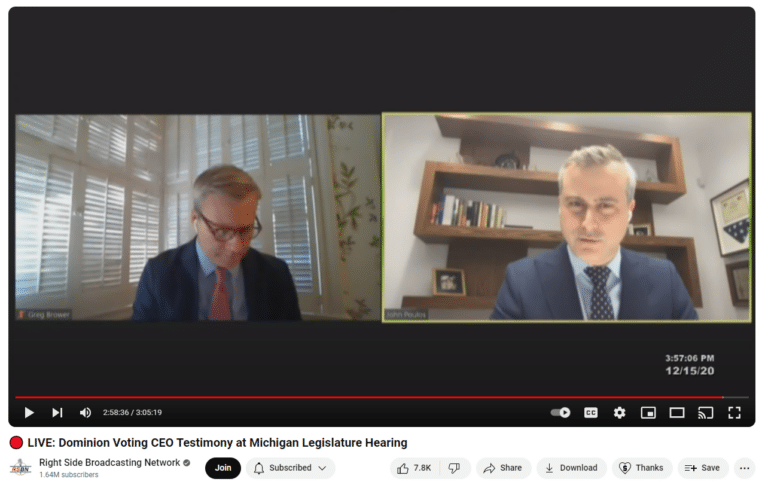
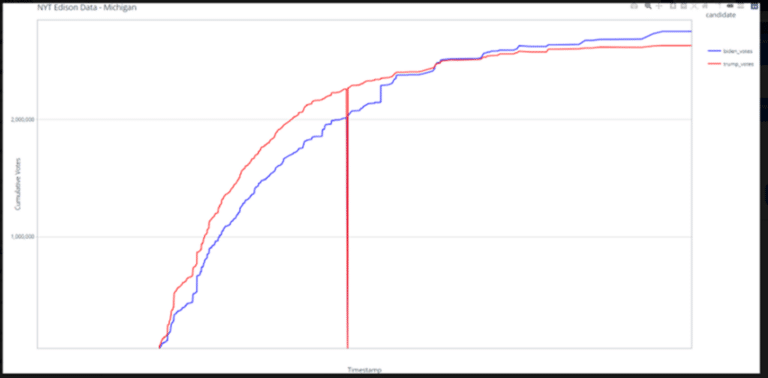
On December 15, 2020, Dominion CEO John Poulos testified under oath with legal counsel present regarding Dominion Voting Systems in use in Michigan during the 2020 General Election. Upon review of his comments against the contents of publicly available records, there are significant grounds to assert that multiple counts of perjury were committed during his testimony. Since his comments served as the basis of many assertions by media and government officials including judges, the veracity of such statements should be examined against the available evidence. On April 16, 2024, the Michigan Grassroots Alliance in cooperation with three Michigan State Representatives filed a criminal complaint with various law enforcement authorities seeking such an examination.
See MGA Criminal ComplaintTechnical Advisory
Election System Risks
CISA’s National Risk Management Center (NRMC) assessed multiple criteria that quantify the scale of election infrastructure cyber risk, including machine preparation, device networking, and the centralization of infrastructure components. CISA NRMC also assessed additional risk criteria related to voter registration, voting machines, and electronic submission of ballots.
See CISA ReportTechnical Advisory
Machine-Based Vote Manipulation
Electronic voting systems have several potential vulnerabilities not found with hand counts. If these vulnerabilities were exploited, the election results could be manipulated resulting in certification of fraudulent results. In order to secure our elections from such exploits, significant security rigor is required. If election officials have insufficient expertise or desire to enforce such rigor, serious consideration must be given to whether or not the risk of the security vulnerabilities introduced by electronic voting systems outweighs their perceived benefits.
Read ECB AdvisoryTechnical Advisory
Government-Sponsored Disinformation
On November 6, 2023, the U.S. House Judiciary Committee and Select Subcommittee on the Weaponization of the Federal Government released an interim staff report examining collaboration between federal agencies and non-government entities to monitor and moderate online speech related to elections. The report raised concerns about potential First Amendment implications of these partnerships and their impact on public discourse.
Read ECB AdvisoryTechnical Advisory
Tabulation Method Comparison
Vote tabulation methods have changed over the years. In recent years, the use of electronic voting systems to tabulate vote totals has gained prominence. Electronic voting systems introduces unique risks to the conduct of elections. Cyberattacks, power outages, and malicious insider threats due to the inability of the general public to monitor the vote tally process are all unique to the tabulation of votes using electronic voting systems. In exchange for accepting these new risks, the general public is told that the use of electronic voting systems is necessary to provide faster results at less cost. This technical advisory will examine the veracity of such assertions.
Read ECB AdvisoryTechnical Advisory
Non-Certified Software
Maintaining the integrity and security of electronic voting systems requires strict adherence to certified configurations and security protocols. Any deviations should be carefully evaluated and approved through proper channels to ensure they do not compromise the system's security or certification status.
Read ECB Advisory